October 23, 2023
Using AI To Enhance Jira And OWASP Dependency-Check
Introduction
Devpost hosted the Atlassian Codegeist Unleashed Hackathon this year from September 05 to October 24, 2023. This hackathon appealed to us at Nautilus Tracker, LLC, for several reasons: first, learning to customize Jira functionality can be a valuable skill to pick up; secondly, and similarly, learning how to integrate various AI tools into human workflows is also a valuable skill to learn.
The stated objective of this particular hackathon is to integrate AI into Atlassian Forge-built customizations.
Of specific interest to us was the possibility of integrating AI into a Jira-based DevSecOps workflow that might help developers better understand, and fix, security vulnerabilities identified by the OWASP Depedency-Check tool, often run in automated CI/CD pipelines associated with software projects.
Here is our video submission demo for the hackathon:
General Impressions
This was our first time working with Atlassian APIs and the Forge CLI and associated UI frameworks. Generally speaking, we found the tools and frameworks straightforward to use in building Jira customizations. Particularly fun to use is the forge tunnel, which allows you to quickly get log statements and exceptions thrown by your application as you run and test your application. Furthermore, forge tunnel facilitates real-time updates to your application in the Atlassian Cloud as you develop, which helps speed up development.
Creating Jira Tickets using the Atlassian REST API is straight-forward as well.
Our specific objective with that was to create bug tickets in Jira associated with security vulnerabilities identified by OWASP Dependency-Check, summarized by the NIST Vulnerability Database, with further summary assistance provided by ChatGPT, in an attempt to see whether this AI tool could make bug remediation more clear and simple to developers.
All of this with the overall hope of making custom software development more secure by improving software supply chain analysis and issue remediation workflows.
Technical Aspects
OWASP Dependency-Check is an Open Source tool commonly used in CI/CD pipelines to help introspect the software supply chain and to identify associated security vulnerabilities. The tool can generate security vulnerability reports in HTML, JSON and XML, etc. It can be difficult for developers, however, to understand the reports or actions required to mitigate the discovered vulnerabilities. The thought for this hackathon was to build a Jira Application that could parse a JSON-formatted Depedency-Check report, summarize the NIST-described vulnerability, then ask ChatGPT to provide a succint summary on how to mitigate the vulnerability specific to the software library that ostensibly needs to be upgraded or otherwise patched.
The Minimally Viable Product (MVP)
We used OWASP Dependency-Check to analyze an existing SpringBoot application and asked it to generate a JSON-formatted report. The report was placed in a publicly accessible S3 bucket that our Jira App could access.
The Jira Application is first asked to access the JSON Dependency-Check file using the fetch API, parse the file, find all dependencies with associated vulnerabilityIDs and an associated NIST URL. If these requirements were met, then then the file name associated with the vulnerability is added to a table to help the developer further triage the identified vulnerability in a simple workflow.
The first step in the workflow consists of a button to execute a routine that will load the associated NIST URL describing and explaining the associated Common Vulnerabilities and Exposures (CVE), and then make the set of CVE Summaries available in a Modal Dialog.
After the CVE summaries (if at least one exists) are retrieved, the next step is to ask ChatGPT if it can further clarify the vulnerability and clearly recommend mitigation strategies that an average developer can understand.
Finally, the developer can create a Jira ticket for the security vulnerability if deemed appropriate, after having assimilated the NIST NVD summary and the ChatGPT mitigation recommendations.
The Architecture
One goal of the MVP was to run the entire application, save the ChatGPT part, in the Atlassian Jira Cloud.
This proved to be a challenge given the time it could take to load and parse all associated NIST NVD summaries; the ChatGPT responses can take even longer to come back at times, often exceeding the 25 second Jira timeout requirement. When an http timeout occurs, the app essentially crashes, which is a less than desireable user experience. We have yet to figure a way around this issue save for running our own service outside the Atlassian environment.
So, as currently built, the timeout constraints are difficult to work around, which necessitated a simplified workflow of doing the processing in discrete, manual steps for each library having an identified security vulnerability in your Software Bill of Materials (SBOM). Even then, timeouts crashes are easily encountered.
In retrospect, while the workflow idiom presented in the UI is sufficient to help vet the idea behind the MVP, it does not provide a good user experience. Ideally, one would want all of the summaries (NIST NVD and ChatGPT summaries) generated behind the scenes first before the developer is presented with them.
The associated Jira Tickets might also be automatically generated as well given an acceptable set of governing rules.
UI
The following is a screenshot of our MVP UI:
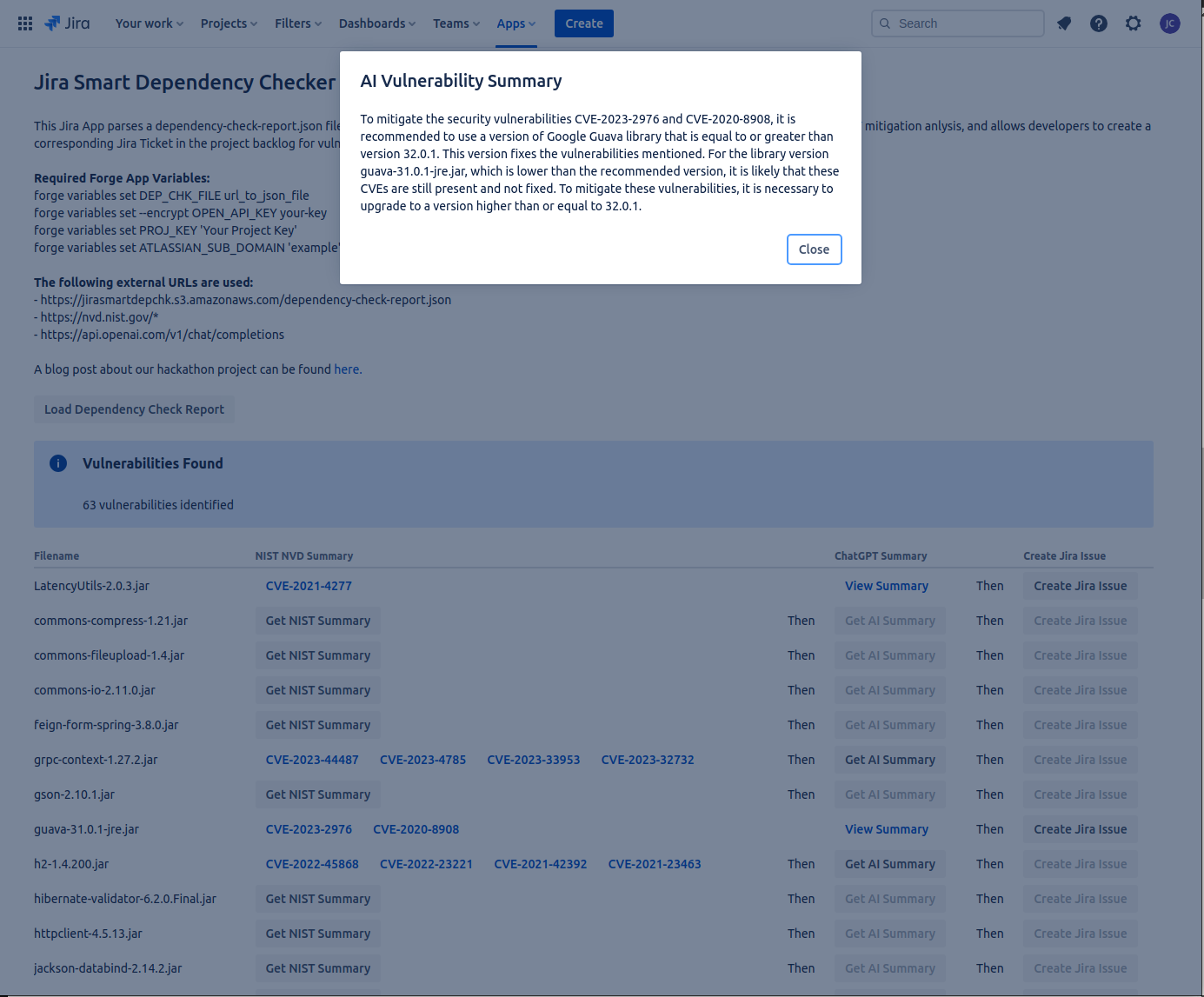
The Forge UI framework was used to generate the UI. If you are familiar with React, then create Forge UI functionality is very straightforward. However, the Forge UI framework offers a somewhat constrained set of components and functionality you can leverage. Atlassian are also previewing UI Kit 2, which seemingly looks like it offers the possibility of pulling-in the full React framework into your UI, but we decided to stick with the tried-and-true framework for our MVP.
Consuming External APIs
We used the Forge API and the fetch function to consume external webpages from NIST. We then used the ‘cheerio’ NPM module to parse the HTML pages read to extract the CVE Summaries found (if any).
We used the OpenAI NPM module to send custom prompts to ChatGPT. Incidentally, no environment or user-specific data was sent to ChatGPT for our analysis, only the CVE and associated summaries.
Again, consuming these external resources over http can take longer than the Atlassian Application environment will tolerate, resulting in the Application crashing. So an obvious improvement to our Application could be the implementation of a ticket-based idiom and hosting the back-end of the Application elsewhere.
The following is an example of what happens to the App when an http timeout occurs:
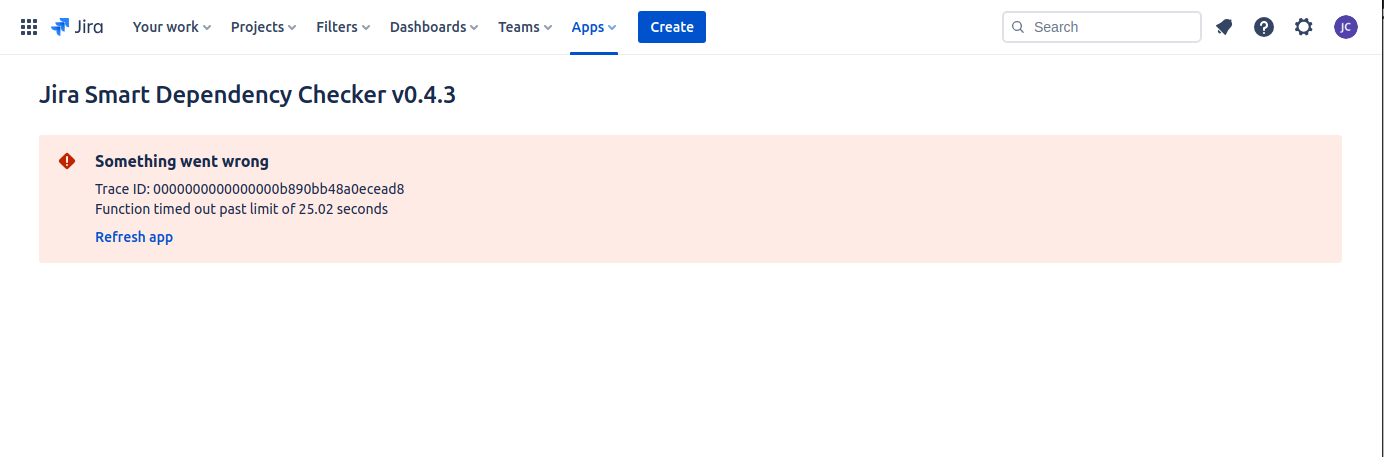
Bummer, dude.
Summary
Participating in the Atlassian Codegeist Unleashed 2023 Hackathon was a great way to get more familiar with not only using the associated Atlassian frameworks and APIs to build customizations on the Atlassian platform, but also to learn how to integrate the burgeoning new universe of AI tools and APIs into existing workflows to see how these new tools might bring new insights, speed time-to-market, etc, etc.
While it was an interesting thing to learn how to use the ChatGPT REST and Javascript APIs, and to integrate it into our MVP for the purpose of helping to summarize CVE mitigation strategies, the jury is still out as to whether this step in the workflow adds much value to the developer in helping to mitigate a given security vulnerability.
However, we think the need for simplifying security vulnerability awareness, descriptions and associated mitigation steps is a worthy objective in helping to shore-up application security in the software supply chain used in custom software development.
Moreover, leveraging Atlassian Jira, OWASP Dependency-Check and AI to help identify and mitigate such security vulnerabilities throughout the SDLC just seems to make sense.
Our Sponsors
Links
James Caple
BLOG
podcast atlassian codegeist hackathon learning hacking javascript react chatgpt forge python devpost ai chatgpt OWASP dependency checker cybersecurity nist national vulnerability database sbom software bill of materials
